Strategies
10 ways BYOD is evolving
A new bring-your-own-device resource from ZDNet called the “BYOD primer for business and IT leaders” is chock full of valuable advice for IT administrators and managers, including common pitfalls to avoid, risk assessments, and solutions for enterprise mobile device management. The guide also lists predictions for how the BYOD trend will play out for the rest of this year and into next.
- BYOD will become more of a requirement than a privilege;
- Full reimbursement for all costs will decrease;
- More apps/cloud resources are coming;
- The Internet of Things will proliferate;
- A unified strategy will be needed;
- Storage may be an issue;
- Security will be harder;
- It will become more difficult to separate employees from the business;
- Employees will need to embrace the previous two concepts; and
- Passwords will fall by the wayside.
Security
For BYOD in the corporate world, the news is a mixed bag when it comes to adoption vs. real-world success. A new report by data-protection company Bitglass found that 72 percent of organizations support BYOD for all or some employees, but relatively few organizations are able to control access to corporate data, remotely wipe devices, or enforce device encryption. On top of that, only 14 percent have successfully deployed mobile application management (MAM) solutions.
“How Forward-Looking Industries Secure BYOD” shares insights on BYOD practices gained from a survey of more than 800 cybersecurity professionals across five major industries, including financial services, technology, healthcare, government, and education.
Key findings include:
- Seventy-two percent of organizations surveyed support BYOD, led by financial services at 74 percent.
- Sixty-two percent of healthcare organizations see compliance as a top security concern, due to HIPAA’s stringent requirements. Notably, organizations across all sectors were concerned with data leakage, including 81 percent of financial services organizations, 90 percent of healthcare organizations, and 79 percent of education organizations.
- Despite regulations and security concerns, fewer than 60 percent of financial services organizations have remote wipe and encryption capabilities.
- Only 54 percent of government organizations support BYOD, a lower percentage than in all other surveyed industries.
- Higher education lags behind other industries in enforcing essential risk-control measures. Only 18 percent of those surveyed have access controls in place, and just 29 percent have the ability to remotely wipe devices.
- Only 14 percent of organizations overall have adopted MAM tools since their introduction in 2010. Most respondents cited employee privacy concerns and usability issues as top challenges to adoption.
Surprisingly, the report found that device encryption was supported in only 36 percent of educational institutions, 56 percent of financial services organizations, and 57 percent of healthcare organizations.
Source: Bitglass
Messaging
Healthcare organizations wanting more control of information sharing and device allocation to their employees have plenty of options also. Security and technical communications problem resolution can seem more manageable when everyone’s got the same equipment – and that equipment is company owned.
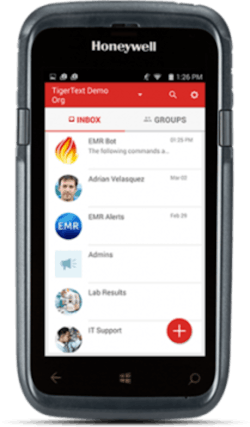
One example for nurses is a hardware and HIPAA-compliant communications software combo provided by Honeywell and TigerText. Honeywell’s new Dolphin CT50h smartphone can now be outfitted with a customized version of the real-time messaging TigerText app. It features secure, encrypted bot technology designed to enable care providers to scan a patient’s barcode to verify identity and then retrieve critical, up-to-date information about the patient’s medications, his or her care team, and the patient’s recent procedures directly from the EMR. The solution provides an efficient and secure tool for sending and receiving protected health information (PHI) as well as other important data necessary for making critical care decisions.
By layering bot technology over the TigerText encrypted messaging platform, healthcare organizations of all types and sizes can automate a wide range of order-related requests while complying with HIPAA and stringent Joint Commission criteria. The TigerText application can be downloaded directly onto the Honeywell Dolphin CT50h from the Google Play Store.
Solutions
Get ultimate security for user-to-user communication
The Avast Virtual Mobile Platform (VMP) takes a fundamentally different approach to enterprise mobility management by focusing on securing data rather than devices. Through ephemeral sessions in which no data footprint is left behind on the device, Avast VMP prevents datajacking, which is the unsanctioned appropriation of data on a mobile handset or computer from the data’s primary owner. Users can make and receive encrypted calls to each other and send instant messages without leaving a trace on devices. It also includes a comprehensive policy engine for greater security, flexibility, and control over apps, data, and users. Avast
Absolute has launched a new service that will reinstall software agents from independent software vendors for existing Absolute customers. Persistence Services enables customers to ensure crucial applications remain installed on a device, regardless of user or location, on or off the corporate network. This service leverages Absolute’s patented Persistence technology, which is embedded into the core of laptop, desktop, tablet, and smartphone devices at the factory by OEMs around the world. From security applications such as encryption and anti-malware, to a VPN client or IT management software, this solution will ensure any business-critical applications are properly installed and operational. Absolute Software Corporation
Have users access your corporate app store
XenMobile is a comprehensive enterprise mobility management solution that manages mobile apps, data, and devices. It is available both on-premises and in the cloud. With XenMobile, users have single-click access to all of their apps from a unified corporate app store. This solution also enables infrastructure and operations professionals to configure, secure, and support many mobile devices, meeting compliance and control needs while giving users the freedom to work the way they prefer. XenMobile received the highest score possible for mobile device management in Forrester Research’s December 2015 Forrester Wave report. Citrix
Dell’s SonicWALL Secure Mobile Access (SMA 11.4) operating system gives organizations the power to easily provision secure mobile access on a global scale, regardless of data type, device used, and/or remote worker location, with a new turnkey approach that ensures secure access of multiple concurrent users. Among its many features, this solution contains patented technology designed to detect malware-infected mobile apps, allowing IT administrators to safely extend their remote service to both the Android and iOS mobile platforms. SMA also allows administrators to quickly provision secure access and role-based privileges to authorized remote workers, contractors, vendors, and temps so they get fast, easy access to approved corporate asset resources. Dell
With the AirWatch 8.4 Enterprise Mobility Management (EMM) platform, employees will be able to access virtually any app with one click in a new mobile experience focused on protecting privacy. One-touch mobile single sign-on (SSO) allows users to access these apps without passwords or complex PIN challenges by leveraging an industry-first SATS (secure app token system). VMware developed the patent-pending SATS technology to enable true SSO across desktop, mobile native, and cloud applications. This unified app catalog will give users consolidated access to corporate apps in a secure mobile application management (MAM) container. VMware
The Managed Mobile Services suite provides an all-inclusive set of mobile device and application management tools to help address the concerns of sensitive data in a mobile environment. Clinicians benefit from knowing their private emails, photos, and personal applications are untouched, while IT administrators can help ensure patient data is secure. These mobile services enforce security requirements for your BYOD policy, while providing IT administrators with access to a real-time, easy-to-use dashboard to manage end-user devices. Managed Mobile Services can be used in connection with either a BYOD or corporate-owned-device strategy. McKesson