Medical identity theft and healthcare fraud is in the news almost daily. HMT talked with several experts regarding their tips on preventing fraud. Healthcare facilities should review how they are analyzing their patient privacy, data security, and fraud auditing programs, as well as their vendor interactions as potential breach areas. We’ve included three sources this issue that look at various approaches.
1. Data security in healthcare: Do you really know your vendors?
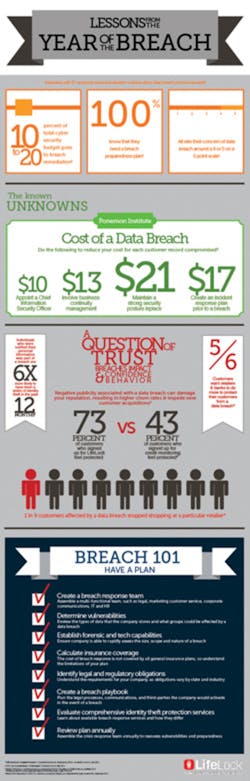
Criminal attacks on hospital and healthcare system data increased 100 percent since 2010 as more organizations move from manual to electronic data storage and sharing. The vast majority of data breaches in healthcare – 70 percent – are due to loss or theft of data, while the remaining 30 percent are due to hacking. Data breaches cost the healthcare industry approximately $5.6B annually, with each individual healthcare organization spending an estimated $2M over a two-year period to address an attack.
The Health Insurance Portability and Accountability Act (HIPAA) Final Omnibus Rule expanded the definition and security responsibility for business associates. Business associates, under the Health Information Technology for Economic and Clinical Health (HITECH) Act, must implement administrative, physical and technical safeguards to protect the patient healthcare data of their customers. More vendors now fall into this category, thus increasing the security risks as more vendors to healthcare organizations touch electronic protected health information (ePHI).
Covered entities must understand and document where and to whom PHI flows. Jackie McGuinn, Sales Effectiveness Director at Vendormate, a GHX company, comments on steps hospitals can take to protect ePHI when conducting business with vendors.
Q. When thinking about data security, what do hospitals sometimes miss?
While many hospitals work to credential vendor personnel who come on-site to their facilities, they often neglect to credential those vendor companies that remain off-site but still have access to ePHI. The increased use of mobile devices by healthcare providers and vendors, including smartphones and tablets, presents the risk that ePHI will be transmitted in an unsecure manner with any number of people accessing, viewing and potentially using this information inappropriately.
To illustrate this point, I was conducting a market research interview with a hospital recently and their director of supply chain told me about a situation where a doctor in the operating room was using an iPad to stream live video of a surgery to a vendor representative who was located off-site so the representative could assist him remotely with the procedure. A third party, not the hospital or the vendor, was facilitating the video stream via the iPad. There are a variety of problems with this scenario from a data security perspective. Because the doctor had no way to know who else besides this representative was watching the streamed video, the doctor and hospital were violating HIPAA regulations. Also, the third party that was facilitating the video stream refused to sign a business associate agreement per HIPAA requirements because the vendor did not want to have responsibility for breach or leakage of ePHI.
Q. What safety precautions can hospitals take to protect ePHI when working with vendors?
Hospitals must understand the flow of ePHI, including within the four walls of the vendor partners. Hospitals should work with a vendor credentialing organization that credentials not only vendor representatives who come on-site but their entire vendor population. When a hospital decides to on-board a new vendor, its credentialing partner should conduct a thorough vetting process to ensure the vendor is legitimate and in compliance with necessary regulations. This process should include:
• Determining which vendors fall under the definition of “business associate,” as defined by HIPAA, and securing agreements with these vendors up front;
• Conducting initial business verification checks for all vendor representatives;
• Performing initial sanction checks (vendor and individuals) to ensure they are not on sanction lists, and subsequent checks every 30 days
• Obtaining documentation for vendor security, training, and data management policies;
• Determining whether vendors and individual representatives have any conflicts of interest that could pose risk for the provider.
2. How red flags, policies and technology can catch medical identity theft
Q. What are the ramifications of identify theft in healthcare?
With patient privacy breaches increasing, hospitals need to take a fresh look at their red flags as they pertain to medical identity theft.
The Federal Trade Commission’s (FTC) Red Flags Rule requires organizations to develop and implement a formal, written identity-theft-prevention program for the purpose of detecting the warning signs, or “red flags,” of identity theft throughout their operations. Red flags are suspicious patterns or specific activities that indicate the possibility of identity theft.
We have all heard about the massive medical identity theft at Anthem, where hackers stole private information of tens of millions of Anthem’s customers. Information included names, birthdays, medical IDs, Social Security numbers, street addresses, email addresses and employment information. Unlike the recent attack at Target, this breach is all about medical identity theft, where hackers use the information stolen from Anthem’s customers’ accounts to impersonate patients. It is speculated that the Anthem breach started in April 2014 and was caught by an Anthem employee in February 2015. This means the breach went on for 10 months.
Setting up red flags in your health organization is a critical function to not only protect patient privacy, but, in some cases, to save lives. If Anthem had red flags and other policies in place, they could have possibly caught the breach earlier before it affected 80 million people.
The worst-case scenario for medical identity theft victims is having their medical record contaminated by someone else’s health information, such as an incorrect blood type or allergies. Even if the fraud is detected, the nightmare has only begun. It can be difficult for patients to flush mistaken information from the system because they don’t know how many databases have their information and which ones need to be corrected.
Q. What are common types of medical identity theft?
The common types of medical identify theft are family fraud, personally identifiable information and electronic records. It is important to build awareness of medical identity theft as a quality-of-care issue in your organization and make patients aware of medical identify theft, which includes using someone else’s medical ID and its consequences. Additionally, healthcare organizations should deploy software for fraud prevention and perform anomaly detection and data flagging. Finally, use appropriate policies and processes so that all red flags are appropriately investigated.
Q. Are you taking the right steps to catch medical identify theft?
Failure to protect patient information contributes to the healthcare industry suffering from the highest number of fraud cases in U.S. history. Most healthcare organizations are neither efficient nor effective at safeguarding Protected Health Information (PHI), leaving themselves open to a tremendous amount of risk. The most notable risk can be damage to the hospital’s reputation and loss of trust from the community and patients they serve.
The problem stems from a lack of understanding about privacy violations and the potential consequences. If healthcare leaders really understood how much PHI access is going on in their facilities, understood the privacy expectation of their patients and fully understood the ramifications, they would reallocate their resources. In addition, healthcare organizations don’t have appropriate staff in place to maintain the privacy program.
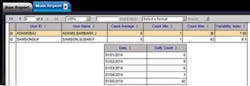
One way to find potential identity theft is to monitor changes to patient records. For example, if a birthdate on a medical record is changed, that should raise a red flag. You need to have a red flag policy in place describing the methods your organization will use to capture this event, and steps for investigation to determine if the patient record has been compromised. It’s impossible to manually monitor these types of red flags, so using technology will allow you to identify and alert on these possible data breaches.
Furthermore, technology will help you use behavioral analysis to determine whether activities fall into an unusual pattern. For example, you can check to see if specific users’ access patterns spike: If a user typically only accesses patient records an average of six times daily, and you see a spike of 40, then this should be flagged to investigate further. Figure 1 represents a report from patient privacy monitoring software that uses behavioral analysis to detect spikes in user access.
With the increasing digitization of healthcare information (in the form of electronic health records) and the formation of health information exchanges, the trend in medical identity theft is likely to continue to rise, as shown with the recent Anthem breach. Personal medical information and PHI is useful to many different types of thieves, which is why it fetches a higher black market price than financial information. The sheer number of targets and the untethered access to patient records also makes the medical sector easy prey. Furthermore, with technology coming relatively late to the health industry, patient privacy and security at health organizations often lags.Once you suspect that there is an instance of medical identity theft, you need to investigate to detect trends and targets for mitigation. That way, you can identify which ones are identity thefts and be able to look for similar instances that could be occurring in your healthcare facility. Also, trend the number of instances and types of red flags, and set up behavioral reports specific to these findings to further analyze possible theft.
Effective auditing cannot be done without automating patient privacy monitoring. There are literally hundreds of thousands to millions of audit events being generated every day in healthcare from all the systems that are being used. Technology is used in all other aspects of our healthcare business, so why not auditing?
There are programs that help automate security audits, such as the Iatric Systems Security Audit Manager. It automatically monitors access to PHI across the entire enterprise and identifies potential privacy breaches 24/7. Information captured by Security Audit Manager enables a more proactive approach to privacy protection across the organization to deter medical identify theft and stop insider snooping. Rather than conducting manual random audits, the program automatically identifies threats and vulnerabilities, assesses risks for likelihood and impact, mitigates security risks, and documents and monitors results. It performs auditing tasks that would require far too many resources to do manually.
With such a solution in place, hospitals can stop struggling with manual audits and be confident that they are doing everything possible to mitigate risk and protect patient privacy.
3. Healthcare organizations lack tools for cyber situational awareness and threat assessment
The Health Information Trust Alliance (HITRUST) has completed a three-month review of its approach to cyber risk management for the healthcare industry. The effort was focused on understanding the challenges of healthcare organizations across varying levels of information protection maturity. The review also focused on identifying approaches and solutions to effectively and practically mitigate and defend against cyber threats and risks.
The analysis uncovered a constant theme: that today’s approach to cyber security is predominantly reactive and, for the vast majority of organizations, inefficient and labor intensive.The analysis also illuminated the fact that, although organizations are increasingly utilizing threat indicators and other threat intelligence, they are doing so without understanding the relevance to their organization. In addition, most organizations are still unable to understand the effectiveness of deployed information security products, especially in relation to emerging cyber threats.
HITRUST CyberVision is the first real-time situational awareness and threat assessment tool tailored to the healthcare industry. Specific findings from the review include:
• Organizations consistently identified a lack of awareness of emerging cyber threats, especially previously unseen attacks, as a key concern. Organizations almost universally acknowledged they had minimal understanding as to the impact of cyber threats on their current cyber security products and the unique applications, systems and devices they protect. This lack of awareness leads many organizations to expend resources and rely heavily on indicators of compromise (IOCs) to determine if a breach or other suspicious cyber activity has already occurred while simultaneously updating rules and policies to block the IOCs. Although valuable, this approach is retrospective in nature and introduces inefficiencies.
• Organizations lack understanding as to the effectiveness of the multitude of products deployed in their environments and lack the ability to communicate, especially to senior management, the effectiveness of their security measures against the probable cyber threat landscape.
The review concluded that, to enable a better understanding of the emerging threat landscape and the impact on organizational specific cyber security defenses, a new approach needs to be deployed and new tools developed. This fundamental shift requires a more proactive model where organizations have real-time situational awareness or insights into emerging cyber threats. The shift also requires the ability to understand the impact of emerging threats on an organization’s specific environment, including layered information security products deployed with custom configurations, as well as industry-specific applications, such as electronic health records (EHRs). This new approach allows organizations to assess the cyber threats relevant to their unique environment down to the applications and system level, so they can use their resources to mitigate the one-to-two percent of the cyber threats that are relevant rather than chasing the 98 percent that aren’t.
Key requirements for real-time cyber situational awareness and effective threat assessment
HITRUST established a comprehensive set of requirements for a service that would address the needs of industry and augment the current reactive approaches with one of proactive insights by delivering these key capabilities:
• Visibility into an extensive degree of current and emerging cyber threats, including previous unseen.
• Ability to evaluate the impact of these cyber threats against the actual security products – network, server and endpoint – currently installed in an organization’s environment.
• Ability to implement multiple configurations per security product and evaluate against default and various tuned configurations, including organization-specific configurations and unique applications.
• Ability to evaluate the effectives of various combinations of multiple security products and benchmark over time.
• Ability to evaluate and assess the risks within minutes of identifying the cyber threat and notifying those affected, based on the products and applications they have deployed.
• Ability to incorporate healthcare-specific applications, such as EHRs, computer control applications for medical devices and organization-specific applications into the evaluation.
• Ability to create best practices – product configurations, including by application.
• Ability to feed threat intelligence and knowledge about which threats are bypassing current countermeasures and security products into the HITRUST Cyber Threat Exchange, allowing for prioritization of resources.
HITRUST met with information security leaders, technology companies, researchers and other thought leaders to identify possible partners and approaches to address these needs. After a detailed analysis, HITRUST has partnered with NSS Labs, a leader in cyber security research and testing, to deliver key capabilities for the HITRUST CyberVision service.
HITRUST expects to have the CyberVision service available in March 2015 including a free subscription level.
Founded in 2007, the Health Information Trust Alliance (HITRUST) was born out of the belief that information protection should be a core pillar of, rather than an obstacle to, the broad adoption of health information systems and exchanges. For more information, visit www.HITRUSTalliance.net.